Codec Networks assist our esteemed customers examine your website pages, applications and web servers to find security weaknesses and vulnerabilities that would not give external threats an opportunity to damage your business.
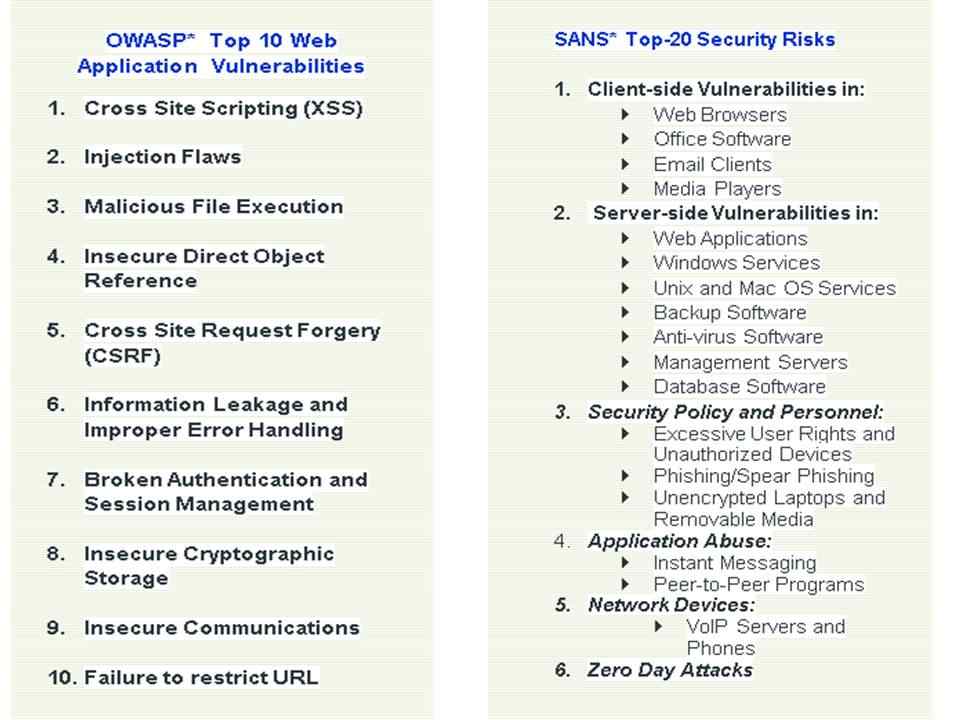
Codec Networks Web Security Assessment and Auditing Services team with web application security testing, vulnerability management and configuration assessment identifies and helps remediate critical web application security threats for all OWASP* Top 10 web application vulnerabilities, SANS* Top-20 security risks as well as various client-side vulnerabilities as follows :
Web Application Assessment And Audit Methodology
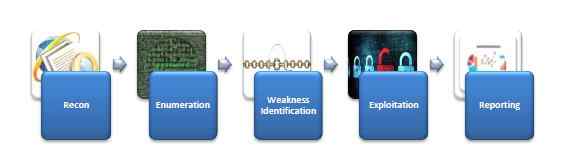
Reconnaissance :
- This involves gathering as much information as possible about the selected application; this is achieved by discovering publicly available information by utilizing a web browser and/or visiting newsgroups, search engines, web resources etc. (in case of information being publicly available).
Enumeration :
This would involve detailing of the target, including but not limited to:
- Application Fingerprinting
- Authentication & Authorization mechanisms
- Enumeration of different types of application pages such as ASP or JSP
- Detecting existing countermeasures against common attacks such as automated form submissions
- Spidering the website. Identify any suspicious pages or pages with large attack surface
- Banner-grabbing
- Ports and services on the webserver
Weakness Identification :
- Automated scanners are utilized to detect vulnerabilities, these tools are further trained using macros and policies are optimized for most optimum scan coverage.
- In addition to tools, an exhaustive list of manual test-cases is utilized to detect vulnerabilities ensuring holistic coverage. Issues like stored XSS, privilege escalations, malicious file uploads etc. that are not detected by automated scanners are identified.
- Best-in-class automated scanners along with manual test cases ensure a thorough coverage including but not limited to OWASP top 10 and SANS top 25.
- Manual verification of the vulnerabilities detected by automated tools is performed to eliminate false positive from the observations. All possible attack and entry points are determined in this phase.
- Immediate notification is raised for high risk vulnerabilities
Exploitation :
- Exploitation of vulnerabilities detected in earlier phases is carried out using exploitation frameworks and scripts, taking a deep dive approach to penetrate as deep as possible. Research is conducted on underlying technologies and infrastructure for known vulnerabilities and exploits that are available in the public domain.
- For production applications, penetration testing is done in a safe mode where payloads are deployed to demonstrate exploitability of vulnerabilities, without actually compromising systems/sensitive data.
- Human intelligence is applied to exploit scenarios that are not comprehended by tools; these could be specific business/functional logics built into the application or exploit instances that require bypassing processes by techniques like social engineering.



