
A Certified Ethical Hacker - CEHV13 Training is a skilled professional who understands and knows how to look for weaknesses and vulnerabilities in target systems and uses the same knowledge and tools as a malicious hacker, but in a lawful and legitimate manner to assess the security posture of a target system(s). The CEH course credential certifies individuals in the specific network security discipline of Ethical Hacking Training from a vendor-neutral perspective.

The Certified Ethical Hacker (CEH V13) credential is the most trusted ethical hacking certification and accomplishment recommended by employers globally. It is the most desired information security certification and represents one of the fastest-growing cyber credentials required by critical infrastructure and essential service providers. Since the introduction of CEH Course in 2003, it is recognized as a standard within the information security community. CEH V13 continues to introduce the latest hacking techniques and the most advanced hacking tools and exploits used by hackers and information security professionals today. The Five Phases of Ethical Hacking Certification and the original core mission of CEH V13 Training remain valid and relevant today: “To beat a hacker, you need to think like a hacker.”
A Certified Ethical Hacker course is a specialist typically working in a red team environment, focused on attacking computer systems and gaining access to networks, applications, databases, and other critical data on secured systems. A CEH Course understands attack strategies, the use of creative attack vectors, and mimics the skills and creativity of malicious hackers. Unlike malicious hackers and actors, Certified Ethical Hackers operate with permission from the system owners and take all precautions to ensure the outcomes remain confidential. Bug bounty researchers are expert ethical hackers who use their attack skills to uncover vulnerabilities in the systems.
CEH V13 Training provides an in-depth understanding of ethical hacking course phases, various attack vectors, and preventative countermeasures. It will teach you how hackers think and act maliciously so that you will be better positioned to set up your security infrastructure and defend future attacks. Understanding system weaknesses and vulnerabilities help organizations strengthen their system security controls to minimize the risk of an incident.
CEH Course was built to incorporate a hands-on environment and systematic process across every ethical hacking domain and methodology, giving you the opportunity to work towards proving the required knowledge and skills needed to perform the job of an ethical hacker. You will be exposed to an entirely different posture towards the responsibilities and measures required to be secure.
In its 11th version, CEH continues to evolve with the latest operating systems, tools, tactics, exploits, and technologies. Here are some critical updates of CEH V13:
CEH V13 is mapped rigorously to important Specialty Areas under the NIST/NICE framework’s Protect and Defend (PR) job role category overlapping with other job roles, including Analyze (AN) and Securely Provision (SP).
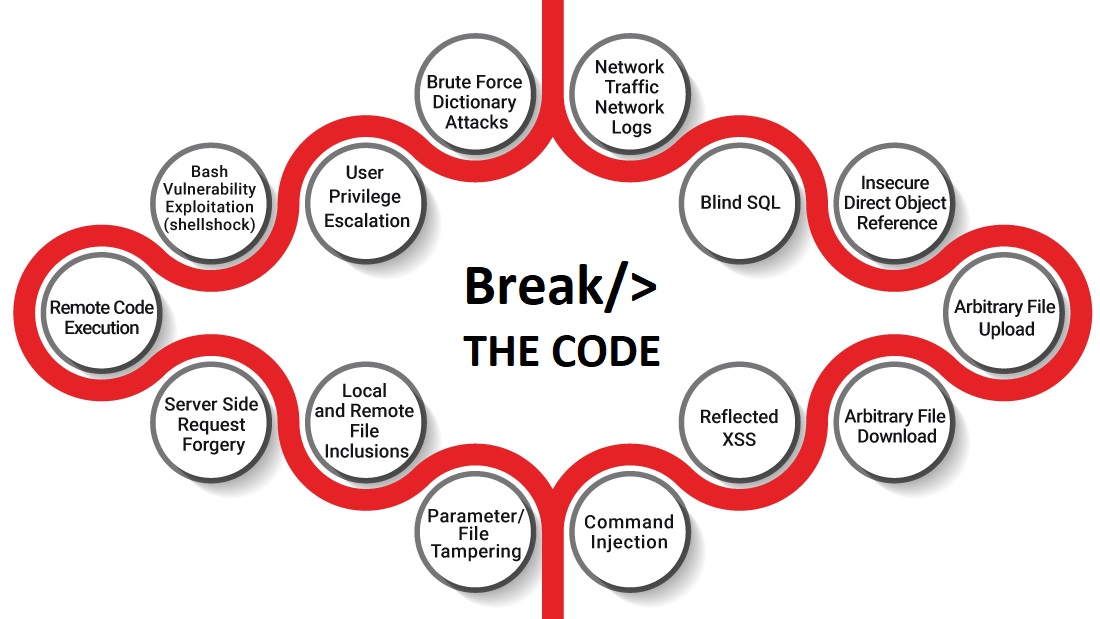
CEH V13 covers updated Cloud and IoT modules to incorporate CSP’s Container Technologies (e.g., Docker, Kubernetes), Cloud Computing threats, and a number of IoT hacking tools (e.g. Shikra, Bus Pirate, Facedancer21, and more). This is critical as the world moves towards broader and deeper cloud adoptions.
CEH V13 now includes the latest malware analysis tactics for ransomware, banking and financial malware, IoT botnets, OT malware analysis, Android malware, and more!
As the security community observed a rise in fileless attacks, it began to raise concerns about fileless malware attacks. As fileless malware is a relatively new form of malware attack, organizations find it difficult to detect with endpoint security solutions. With the CEH V13, you can now learn various fileless malware techniques with associated defensive strategies, as the course focuses on the taxonomy of fileless malware threats, fileless malware obfuscation techniques to bypass antivirus, launching fileless malware through script-based injection, launching fileless malware through phishing, and more.
This latest iteration of CEH V13 includes new operating systems, including Windows Server 2019, Windows Server 2016, and Windows 10 configured with Domain Controller, firewalls, and vulnerable web applications for practicing and improving hacking skills.
More than 50% of the CEH V13 course is dedicated to practical skills in live ranges via EC-Council labs. EC-Council leads in this aspect of the industry.
The CEH V13 course includes a library of the latest tools required by security practitioners and pen testers across the world.
C|EH Master, is the next evolution for the world-renowned Certified Ethical Hacker credential, and a logical ‘next step’ for those holding the prestigious certification. Earning the C|EH Master designation is your way of saying, “I learned it, I understood it, and I proved it.”
Codec Networks provides the Best Ethical Hacking Training. Here we have an environment exactly like the actual one where they will be taught how to perform information gathering, scanning, getting access i.e. hacking, maintaining access, clearing tracks as well as how to secure their own networks. We have intensive lab environment where the student will gain practical knowledge with reference to the current security attacks and threats scenarios well-built simulated lab where the students can perform the practical under the supervision of experienced trainers who are working in the cybersecurity domains. The whole concept is to provide practical knowledge along with concept clearing in Cyber Security which is useful from career perspective in the organisation as well as for the security enthusiasts, entrepreneur. At the end of training students will have a good understanding and hands on experience in IT Security.

C|EH Practical is a six-hour, rigorous exam that requires you to demonstrate the application of ethical hacking techniques such as threat vector identification, network scanning, OS detection, vulnerability analysis, system hacking, web app hacking, etc. to solve a security audit challenge.
This is the next step after you have attained the highly acclaimed Certified Ethical Hacker certification.
Professionals that possess the C|EH credential will be able to sit for exam that will test them to their limits in unearthing vulnerabilities across major operating systems, databases, and networks.
You will be given limited time, just like in the real world. The exam was developed by a panel of experienced SMEs and includes 20 real-life scenarios with questions designed to validate essential skills required in the ethical hacking domains as outlined in the C|EH program.
It is not a simulated exam but rather, it mimics a real corporate network through the use of live virtual machines, networks, and applications, designed to test the your skills. You will be presented with scenarios and will be asked to demonstrate the application of the knowledge acquired in the C|EH course to find solutions to real-life challenges.
C|EH Master, is the next evolution for the world-renowned Certified Ethical Hacker credential, and a logical ‘next step’ for those holding the prestigious certification. Earning the C|EH Master designation is your way of saying, “I learned it, I understood it, and I proved it.”